Summary
Article Name
Securing your website: Essential tips for linux VPS hosting
Description
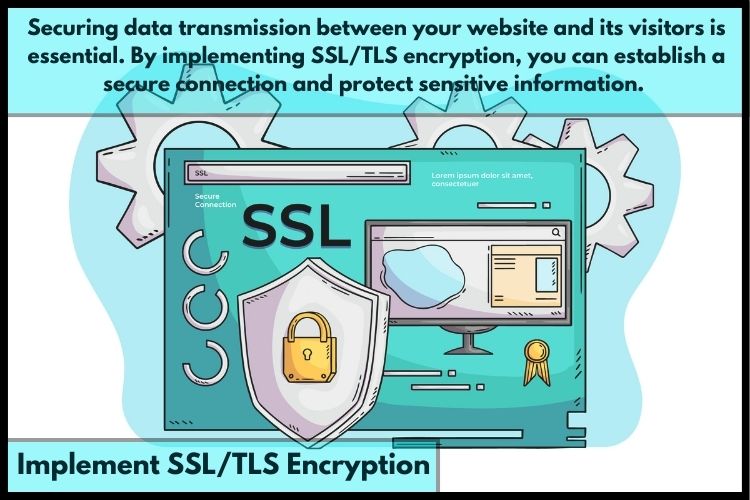
Website security is crucial in today's digital environment. As a website owner, it is crucial to ensure that your Linux VPS hosting environment is secure and protected from potential threats.
Author
Rahil
Publisher Name
VPS Linux Hosting
Publisher Logo